What is Ransomware?
Without exaggeration, ransomware is a disaster. To some extent, it is worse than any virus. You can heal your device if it gets infected by a Trojan, for example. But there is hardly anything you can do to rescue your folders affected by ransomware. It will encrypt them. You will know that the documents are there but won’t be able to access them. Unless you choose to give a ransom to the cybercriminal.
Ransomware definition and variations
So, we are talking about malware that codes files on a user’s computer or locks it out. It is among the most popular harmful programs. Ransomware may have different shapes and sizes. But there is one goal in common: to demand a ransom. And hackers are ready to spend days and nights creating new types of this type of malware. Obviously, the scheme brings money quickly.
How does ransomware work? Well, there are two basic kinds of ransomware: encryptors and screen lockers. Encryptors code your files. Instead, screen lockers take over the OS and would not allow access to your device.
Nowadays, encryptors seem to be the most effective. Some of them not just encrypt files but also delete them. For instance, Jigsaw. This malware would erase your files till you pay the ransom. It would first tease you erasing several files every hour within a 72-hour period. And if you do nothing, all folders will be gone forever.

Here are some forms of ransomware:
- Scareware. This malware uses social engineering actively. The goal is to convince the user to visit an infected website or buy software which looks like an antivirus, for example. Some types throw out pop-up messages and alerts to your screen. Some kinds of scareware may lock users’ computers but usually, it affects their files.
- Doxware. One of the most profitable attacks for hackers. This is a combination of malware and a personal data leak. Hackers menace to make private photos, conversations, and sensitive files public unless the ransom is paid.
- RaaS. This model reminds of an MLM. The network members don’t even need special technical knowledge to distribute the software. One of the most famous examples is Cerber. The ransomware is relatively new but it has already affected millions of users. Its decryptor is compatible with 12 languages. Affiliates get 60% of the profits and enjoy an additional 5% for a new recruiter. The scheme uses a Bitcoin account to launder the money.
How does ransomware infect your computer?
There are several ways how malware manages to master your machine. It often utilizes phishing spam – email attachments which users believe to be trustworthy. Once you open the attachment, your computer is infected. And there is hardly anything to do with that.
Social engineering tools are among the hackers’ favorite. They play with users’ emotions to gain administrative access to their devices.
Malvertising is another method to deliver malicious software. Hackers will even invest in ad space on YouTube and wait till you find it.
But there are also aggressive ways to infect computers. These have nothing to do with users’ behavior really. They rather search for security holes to infect devices.
Once it gets inside, different ransomware has different strategies to spread. But at the end of the process, they will make any further work with your files impossible. Unless you pay for a mathematical key to decrypt them or unlock your computer.
Some hackers even try to look decent claiming that they are a law enforcement agency. They send a message that the victim violates the law utilizing pirated software, for example. And then they demand to pay a “fine”.
Can you become a target?
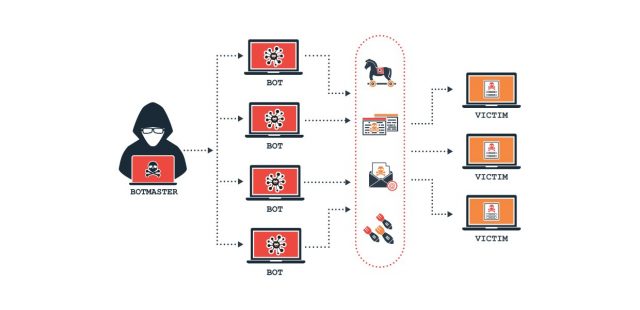
A ransomware attack is usually more targeted than malware. Big organizations are of particular interest since they are more likely to pay the money. Nevertheless, anyone can become a target. One of the most massive attacks by WannaCry hit more than 200,000 users around the world. It became possible due to Windows vulnerability.
But as it has been already said, company and organizations look more attractive to hackers. Usually, they use custom made software which needs a special approach to updating. And since there are many computers to take care of, not every organization pays enough attention to that. Also, some entities lack funds for adequate antimalware. For example, hospitals which spend money on saving people’s lives and not computers. But once hit a by ransomware, they are likely to pay a cybercriminal for restoring their patients’ histories.
How do I know if my device is infected
Often after a ransomware virus settles inside of your computer, it shows no signs of presence. You keep on using your files as you always do. But the malware is not sleeping. It is communicating with the hacker’s server and creating two keys – one to encrypt your files, the other – to decode them. As you can guess, you won’t have the last one till you pay for it. The described process is short. You will find out that you are in trouble soon. A ransom message will show up on the screen explaining the situation and describing your next steps.
Most of the time, you get 72 hours only to pay the money before it gets too late to save your data. And don’t waste your time trying to open your docs. There is no chance to do that without the decoding key.
How to clean your computer

Whether you choose to pay the money or not, you must still know how to remove ransomware. If your machine is not locked, you should follow the same steps as with deleting any other malware or virus. Basically, your actions should go as follows: reboot Windows to a Safe Mode and get rid of the malware either manually or with an antivirus. Restore your PC to a previous state.
You are in bigger trouble if your PC is locked. If this is a case, there are three ways for ransomware removal:
- implement a System Restore and return to the state when your PC was safe;
- use an antivirus from an external drive or bootable disk;
- reinstall the whole OS.
You may also consider contacting an IT specialist for help.
But remember, you won’t get your files back! In fact, the above measures will rescind the possibility to restore your files because you will get rid of the ransomware from your machine. And thus, the option to pay money will be gone.
How to get your files back
Unfortunately, in most of the cases with ransomware, there is no way to get your files back to a normal state without the decoding key. With this thought in mind, the logical question is whether you should actually pay a ransom.
Should I pay to recover my files?
Paying the hacker seems the only solution in case your device is infected. But is it really a good one? Majority of attackers do not charge too much. Relatively. Last year the average ransom was about $522. But the price is too high for being naive. Also, there is no guarantee that they will actually send the recovery key once you pay them. They are criminals, remember?
The best thing is to defend your PC and never face the necessity to decide whether to pay the ransom.
How to Protect Your Computer from Ransomware

There are several measures you can (and should) take to close your device for any kind of malware and reduce the potential harm if it still manages to get in:
- Install an antivirus. Majority of modern antivirus software is capable of resisting any ransomware attack. Purchase one of those to defend your device. Don’t forget to update it regularly, otherwise, it is almost useless.
- Update your OS. Timely OS updates will have to remove vulnerabilities on your device. This gives fewer chances to hackers to approach your hard drive.
- Never open email attachments automatically. As mentioned, ransomware often arrives with attachments. Needless to say that you possess all the power to avert it from getting into your machine.
- Never install unauthorized software. You should always be 100% sure about every new program on your PC.
- Make backup copies of your files. Use cloud services or portable devices. The best thing is to have files copied automatically. Obviously, this step won’t stop ransomware. But if you can restore your files, would you be too stressed out about losing them?
Ransomware attacks in 2019-2021
According to Kaspersky’s Ransomware and Malicious Cryptominers 2016-2018 report, ransomware infections decreased 30% over one year. Probably, the reason is that the majority of victims refuse to pay the ransom. Or they simply don’t have quick access to cryptocurrency. No matter what the reasons are, seems like some cybercriminals are turning into crypto miners.
However, this doesn’t mean we can relax. The hackers who still prefer ransomware as their primary source of income, become more proficient. Besides, it is not clear yet whether the minor boom will last. We all have to be aware of the risk of being infected and should always take precautions to stay secure.
What is ransomware: video tutorial
Other links
Directory of UK Security Companies – Business listings for security companies and locksmiths.