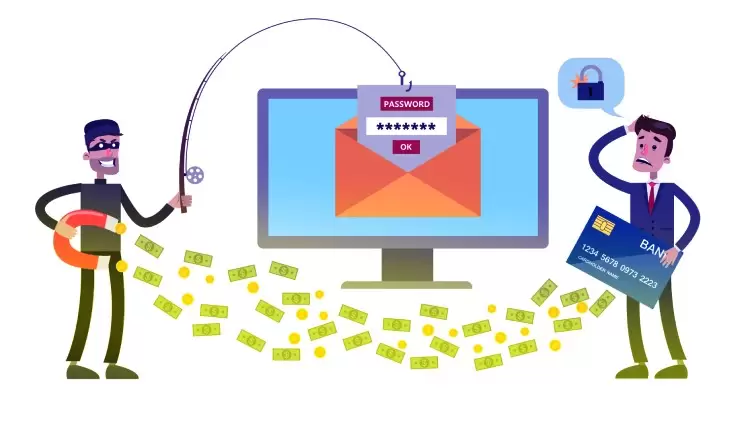
To put it in simple words, spoofing is when a cybercriminal tricks the user into believing that he/she is communicating with a trusted source. Spoofing is mostly used to obtain personal data, re-direct traffic, and even infect the victim’s device with malware. Hackers spread malicious files through attachments and links. It’s not rare for them to apply to spoof as a means of taking over the user’s computer to start an even more massive attack.
Not only home devices are in danger: corporate data centers are even more attractive targets to the criminals. A successful spoofing attack on an organization can lead to leaks of sensitive data, hurt their reputation, and more. And now that we’ve learned what spoofing is, let’s take a quick look at its various types.
What Is an Example of Spoofing?
Emails, direct phone calls, specific websites, IP addresses, DNS servers – those are just some of the areas that cybercriminals use for spoofing. It all comes down to the means of communication and the way the fraudsters try to get access to remote devices. Next, we’ll discuss eight examples of spoofing. Learn more about each not to become a victim.
Email Spoofing
This is when the criminal sends an email message, making the user believe that it came from a person he/she knows and trusts. Mostly, these types of emails are infected with malicious attachments and links. Also, an email spoofing attack can use so-called social engineering and gain personal/sensitive info from the recipient.

According to official statistics, this is one of the most popular forms of spoofing that affects numerous users around the world. The best way to realize that you’re dealing with an attack is to check the email address. Chances are, there will be slight mistakes there. Usually, email spoofing is used to request financial transactions or access to a well-protected system.
Caller Id Spoofing
These days, it is relatively easy to make it look like a phone call is coming from a specific number. It can be a familiar number, one that the recipient trusts and won’t question, or a number that is originating from a specific location. This is what Caller ID spoofing is all about. Again, tricksters use social engineering and claim they’re from the bank, the government, or support.
Then, they ask the victims to share sensitive information, such as logins, passwords, credit card information, account credentials, SSN (social security numbers), and more. It would be best not to answer these kinds of questions over the phone, even if it is, indeed, a legit person calling you.
Text Message Spoofing
AKA “SMiShing,” or SMS Phishing, text message spoofing works almost precisely like email spoofing. Only this time, instead of sending you an email, cybercriminals send text messages to your phone (pretending to be your bank, for example). Don’t click any links inside these messages or call any phone numbers unless you’re 100% sure they can be trusted.
Website Spoofing
This refers to when the attackers take the design of a popular website and create an exact copy of it. Usually, it is a site that the user knows and trusts (and visits regularly).
The goal with website spoofing is to make the users believe it’s the real thing and enter his/her personal information. As soon as they do that, the criminals obtain the logins-passwords and steal money or sensitive data.
Many modern-day antivirus products come with built-in anti-keyloggers that make it impossible for anyone to track your keystrokes. Still, be vigilant, as it is very easy to be tricked into thinking that you’re on a trusted, secure website, when, in reality, you’re about to give away your credentials.
IP Spoofing
An IP Spoofing attack is used to hide the actual IP address and the identity of the sender. Impersonation is another way to make you believe it’s a person that you know and trusts on the other side of the communication. While email, phone, SMS, and website spoofing aims at the user, IP Spoofing centers on the network. It’s when the bad guys are trying to get access to a restricted system by impersonating an IP from the same internal network.
If you don’t have access to a closed system, you’ll probably never have to deal with an IP Spoofing attack. Corporate businesses, on the other hand, mostly suffer from this exact type of spoofing. Developers of antivirus solutions know about it and continually update their databases to keep IP attacks at bay.
ARP Spoofing
Here’s where things get a little bit complicated: ARP, AKA the Address Resolution Protocol, works in a union with MAC (Media Access Control). ARP resolves user IP addresses to MAC addresses – that’s how data is transmitted between the two. ARP Spoofing is when a criminal links his/her MAC to a legit network IP address.

Therefore, they can get right between the transmission and access data that was intended for the owner of that IP address. Session hijacking, stealing/modifying data, and man-in-the-middle attacks are the most common “treats” of ARP Spoofing. It is very hard to recognize if you’re a regular user.
DNS Server Spoofing
Domain Name System servers have many similarities to the ARP. They are busy resolving email addresses and website URLs to the respective IP addresses. DNS Spoofing is a technique that allows the attacker to re-route the traffic to an IP address of his/her choosing. That takes the victims to malicious websites that are quick to infest their devices.
Protect Yourself Against Spoofing

Now that we know how spoofing works, it’s time to talk about the ways you can protect yourself:
- Don’t be overly trusting: always check when something seems suspicious to you
- If you get an email that doesn’t look legit, a phone call will allow you to confirm that you are, indeed, dealing with the actual sender
- When visiting a website for the first time, keep an eye on how it behaves and don’t enter any personal info into any of the fields
- Make sure you have a decent antivirus solution installed: it will be of great help
- Pay attention to the email sender’s address (if it’s spoofing you’re dealing with, some of the letters might be wrong)
- The same goes for the URL of a website page (look closely: aren’t there any wrong letters there?)
- Unusual turns of phrase and lousy spelling can reveal a spoofing attack
- Don’t ever download any “shady” attachments or follow any links. Send a quick reply to confirm that it is indeed the “owner” of the email sending you these
- Avoid taking a call at face value and don’t give any straight answers. We recommend hanging up and calling that exact number yourself to save yourself from caller ID spoofing.