CryptoLocker is a notorious malware that poses severe threats to companies that specialize in data processing. Its first attack was recorded in September of 2013. The target of the attack was computers using Windows operating systems.
According to records, the attacks did not occur up until the end of May in 2014. From this period, new variants of this malware emerged. The new variants are even more sophisticated. They can easily beat anti-malware programs and most firewall technologies, hence the reason for concern.
CryptoLocker Ransomware Threat
Generally, CryptoLocker is classified as ransomware. This is because cybercriminals use it to swindle money from victims in the form of a ransom.
CryptoLocker threat type
After cybercriminals have launched the Crypto virus into a specific network, it locks all files on the system mains and endpoint devices. To regain access to their data, the company or individual would have to pay a certain fee/ransom.
What are the symptoms if my PC is infected with Cryptolocker?
Soon after CryptoLocker has attacked a user (individual or organization), it announces its presence through a ransom note. This note will give the victim a set of instructions regarding the payment method. It also asks them to reinstall the ransomware if it has been deleted by the computer’s antivirus.
The victim will also lose access to their files on the computer (or computers in that network). CryptoLocker will add various extensions to files to render them unusable. Unless payment is made (usually in cryptocurrency), it’s possible to lose the files completely. At this stage, users usually blame themselves for making such a silly mistake or not having the Software for Malware Protection.
How Cryptolocker distributed?
This ransomware can enter secure networks in many ways. It can find its way through email messages, downloads, and file-sharing sites. These are common means that hackers use for spoofing. Thus, it is important to only use trusted download sites and to never open links in spammed messages.
Cryptolocker Ransomware Removal Guide
To protect or recover your files, you can use antivirus software such as Total AV. This software has a better chance of defeating the ransomware. Alternatively, you can use a decryptor tool or run your backup files.
How to Remove CryptoLocker Ransomware with Total AV?
You can effectively remove CryptoLocker from your device by using Total AV antivirus, for some, the best antivirus on the market. This cybersecurity solution can expunge it from your computer. There is such an option as a Scan, which may detect the malware.
Here is how to use it:
- Install the Total AV antivirus on your PC.
- Complete a Full Scan by clicking the appropriate button on the dashboard.
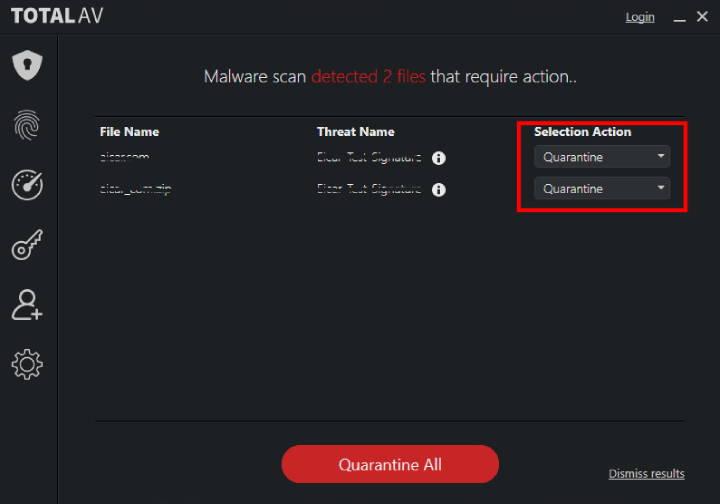
- After the software finished the scan, you will be given a list of threats (the pic above).
- On the right side, you will see the “Action” blocks. From the variety of options, pick the one called “Delete” for the newly discovered threat.
On the other hand, Total Av as well has a real-protection feature. It usually identifies the attack on the computer if installed on your computer at the moment of the intrusion.
However, deleting this ransomware may not be sufficient. The developers of CryptoLocker knew this would happen, and they ensured that deleting the ransomware would never result in the decryption of your files. You will need to use the correct key to unlock your files.
What’s then the use of an antivirus?
Total AV software minimizes the damage that can be caused by ransomware. After CryptoLocker has found its way into your computer, Total AV will bust it and remove it before it has encrypted all your files. Thus, although you may lose some data to the cyber attack, the damage may be minimal.
How to Remove Cryptolocker Ransomware by Yourself on Windows 10
As mentioned before, you can remove CryptoLocker by using an antivirus solution such as Total AV. Besides, you can appeal to the best free online and desktop virus scanners for its identification. But, if you take CryptoLocker as a personal challenge, there is another way. It will require you to have all your data backed up. Without a backup, you will risk losing everything.
You can use the System Restore feature that comes with Windows computers. This feature allows you to return your device to an earlier time before acquiring the malware. However, this may not necessarily decrypt your data. Another thing you can try is to reformat your hard drive. This move will erase everything on your PC, including the encrypted files. Afterward, you may then run your backup to restore your files.
There are specific ways to remove the ransomware on Windows 10. The first method contemplates utilizing the Safe Mode With Networking and further scanning the computer with anti-malware instruments. The second one is concerned with the restoration of the backup, which is only possible if you have a previously restored copy of data. That’s why many sources insist on backing up your files.
Notably, in the case of CryptoLocker, both methods are necessary to perform to make sure that the malware is gone.
First step: Safe mode
1. First, find the power button in the left corner of your desktop, pick “Restart” while holding “Shift.”
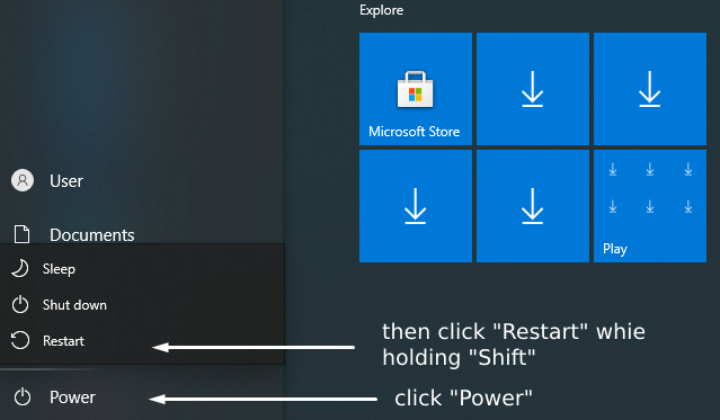
2. Then, pick the “Troubleshoot” option. After it, click “Advanced Options” and proceed with “Startup Settings.” There, you will have a list of options. On your keyboard, push the F5 button to initiate the “Safe Mode with Networking” option. Lastly, “Restart” your computer.
3. Now, you can try to delete the CryptoLocker with the “Task Manager”. You will have to find the program via the search bar at the bottom of the screen. Find there CryptoLocker, disable it and remove it. At this stage, it is better to download a decent antivirus like TotalAV or Norton 360 and delete all the suspicious files under this mode.
However, there is a chance that the virus will still remain in your system. Thus, restoration of the system may be inevitable.
Second step: Restoration of system files
To do so, you will need to activate the previous backup available on your computer. In other cases, all your files would be deleted. What should one do next?.
1. Open the “System Protection” Window within the System Properties.
2. Then, find the “System Restore” category on the upper side of the window. Click on it.
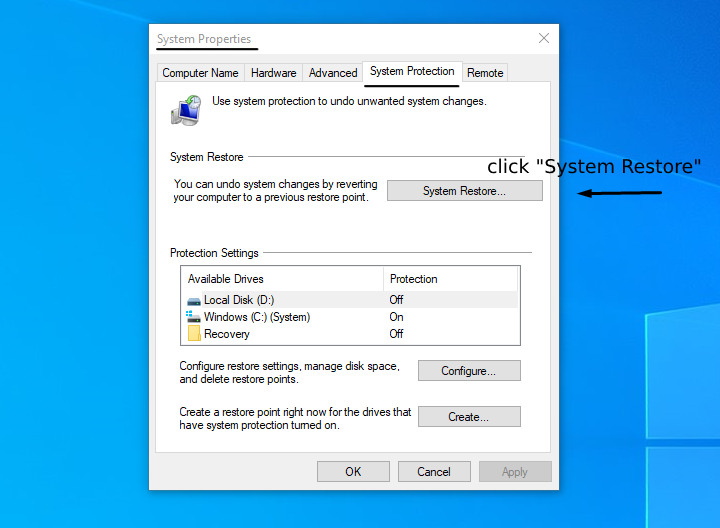
3. It will launch the restoration process. At this stage, click “Next” and follow the guidelines.
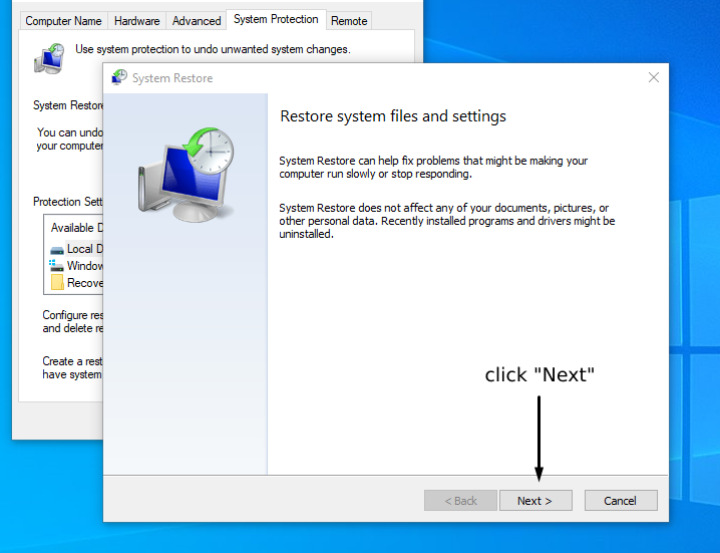
4. Now, you will see the restoration points. Pick the last one relating to the period when your computer was not contaminated with CryptoLocker.
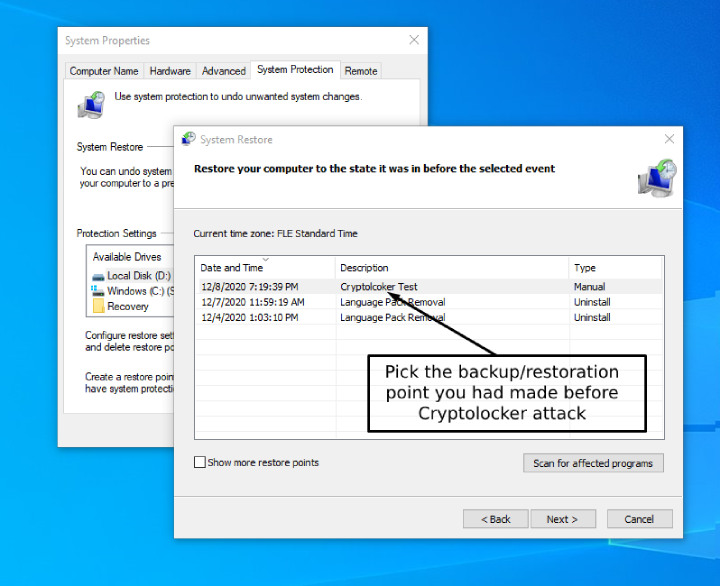
This is why you need to regularly make backups of all of your files and avoid losing all the files when such a virus hits. If you are not ready to lose the data, try finding a decryption tool for CryptoLocker. Just for you attention, McAfee, despite being a decent antivirus, provides a free decryption tool for your service.
5. When you are ready, click “Finish” and the program will restore the previous version with no CryptoLocker on it.
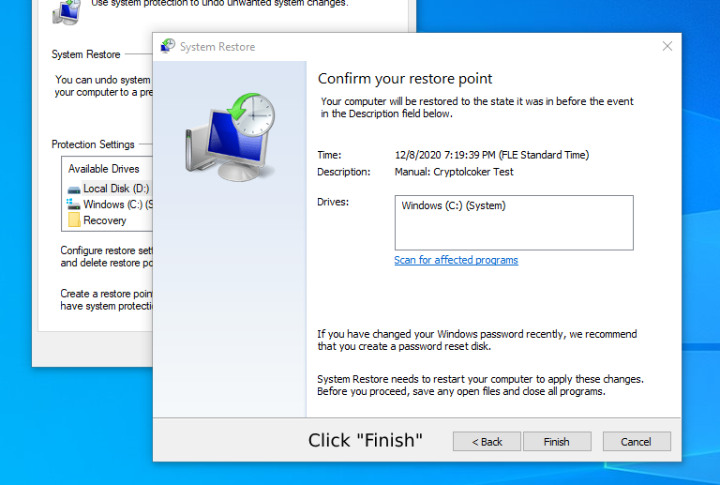
Next, to prevent future threats of that kind, it is better to find a proper antivirus solution suitable to your needs, whether it is Total AV, PC Matic with its white-listing approach or another solution for Windows 10. Besides, there are free options, too, if you, as a user, not ready to pay for protection. Remember to make restoration points or backups even if you have the highest and most advanced protection.
NB: Reformatting your hard drive requires a certain level of expertise. Don’t rush into it unless you’re knowledgeable enough and know what you do.